I guess I have been a lucky guy over the years because it seems like I can count on one hand the times I've been the victim of a computer virus infection. I got one last week that was rather embarassing.
It started with a message from a friend on Facebook:
Heey! You are on TV!
http://bit.ly/1IqQhl
DON'T CLICK ON THE LINK! My first mistake was to click on the link. This is one of those shortened Urls that Facebook and some of the social networking sites prefer so Urls will stay short and not clog up their server storage space. The obvious problem is that you have no idea where this link is taking you. You'll see from the screenshot below that link takes you to 98.121.143.232, which is assigned to rr.com, one of the sites (probably a shared web site) hosted by Road Runner. Most likely this was a site owned by someone who fell victim to this same virus, which hacked their site.
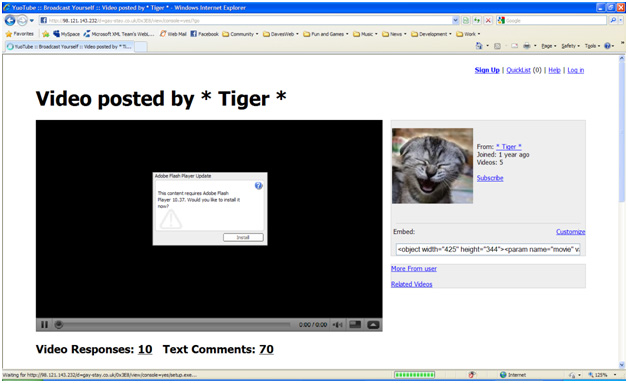 |
| Screenshot of the message that had links to a virus installer in it--click anywhere and you're infected |
My next mistake was clicking on the Adobe Flash Player Update's Install button. First, I should have been tipped off by the version number: 10.37. Adobe Flash's version numbering doesn't work like that. The latest version of Flash is 10.0.32.18, but who is going to go check the version first? Not me. I clicked and that kicked off the virus installation. Later, I determined that most of the message I saw, with the video player and the Adobe Flash Update pop-up was all a big gif image. If I clicked ANYWHERE on the page, I would get infected. And even if I didn't click anything, if I clicked on any of several pop-ups that appeared automatically, I would get infected.
The virus was W32.Koobface.D, which has apparently been going around Facebook for several months. Idiots like me keep on clicking on this bogus message and getting infected.
W32.Koobface.D is a worm that propagates via social networking websites by creating a malicious links that will lead to an infection. W32.Koobface.D may gather sensitive information on the compromised computer and sends it to the remote attacker.
www.precisesecurity.com
Threat Assessment: Wild
Wild Level: Low
Number of Infections: 0 - 49
Number of Sites: 0 - 2
Geographical Distribution: Low
Threat Containment: Easy
Removal: Easy
DamageDamage Level: Low
Payload: Spreads through social networking sites.
Releases Confidential Info: Gathers authentication cookies and sends them to a remote location.
DistributionDistribution Level: Low
www.symantec.com
 |
| The new and improved Koobface fake message |
And I apparently didn't even get the new and improved version of Koobface, which sends a different message with every infection, appending random text at the end of its note, and using a Flash Upgrade prompt that doesn't list the version number (making my visit to Adobe's website to get the latest version a useless task).
The embarassing thing was the Koobface sent a similar message to all of my Facebook friends. And, as you might expect, out of my hundreds of friends, a few got infected.
The thing that was not embarassing at all, but potentially disastrous, was that Koobface apparently stole my cookies. That's how it was able to use my Facebook account to send messages. Fortunately, I realized pretty early on that I had been infected and I changed my Facebook password. That may have minimized the damage.
It was when I was working on my website that I realized that Koobface was able to hack into my web hosting account. Fortunately, the virus didn't do anything to my existing web site. But it did install a folder and a couple of files on my web site. It created a folder named 883 and added an index.php file and a gif file that was identical to the screenshot above. I deleted these files--and quickly--but I regret that I didn't stop to examine these files.
I figured that newly-infected browsers would eventually come back and hit these virus-installed files on my site. The next day I checked my server logs and, sure enough, I found evidence that the Koobface command center was checking to see if my site was still infected. These two requests were logged:
It looks like the first request was to see if the /883 folder was still there, but the server responded with 403 - Forbidden because directory browsing is not allowed on this web site. The second request is for the /883/index.php file, which the server apparently located successfully and served up to the browser. However, because PHP isn't installed on this machine, the server just returned the text of the PHP file, which was pretty small at just 58 bytes. This must have been enough evidence to the virus that PHP won't work here becuase I have seen no other requests for anything in the /883 folder since then. Note that they covered their tracks by faking the http headers so as to not give away any information about their browser/UserAgent.
In retrospect, I was stupid and should be more careful. If you don't know what it does, don't click on it! But Koobface is a cleverly-crafted virus. Even if you followed all of Symantec's recommended security "best practices", you still might get infected:
- Use a firewall to block all incoming connections from the Internet to services that should not be publicly available. By default, you should deny all incoming connections and only allow services you explicitly want to offer to the outside world.
- Enforce a password policy. Complex passwords make it difficult to crack password files on compromised computers. This helps to prevent or limit damage when a computer is compromised.
- Ensure that programs and users of the computer use the lowest level of privileges necessary to complete a task. When prompted for a root or UAC password, ensure that the program asking for administration-level access is a legitimate application.
- Disable AutoPlay to prevent the automatic launching of executable files on network and removable drives, and disconnect the drives when not required. If write access is not required, enable read-only mode if the option is available.
- Turn off file sharing if not needed. If file sharing is required, use ACLs and password protection to limit access. Disable anonymous access to shared folders. Grant access only to user accounts with strong passwords to folders that must be shared.
- Turn off and remove unnecessary services. By default, many operating systems install auxiliary services that are not critical. These services are avenues of attack. If they are removed, threats have less avenues of attack.
- If a threat exploits one or more network services, disable, or block access to, those services until a patch is applied.
- Always keep your patch levels up-to-date, especially on computers that host public services and are accessible through the firewall, such as HTTP, FTP, mail, and DNS services.
- Configure your email server to block or remove email that contains file attachments that are commonly used to spread threats, such as .vbs, .bat, .exe, .pif and .scr files.
- Isolate compromised computers quickly to prevent threats from spreading further. Perform a forensic analysis and restore the computers using trusted media.
- Train employees not to open attachments unless they are expecting them. Also, do not execute software that is downloaded from the Internet unless it has been scanned for viruses. Simply visiting a compromised Web site can cause infection if certain browser vulnerabilities are not patched.
- If Bluetooth is not required for mobile devices, it should be turned off. If you require its use, ensure that the device's visibility is set to "Hidden" so that it cannot be scanned by other Bluetooth devices. If device pairing must be used, ensure that all devices are set to "Unauthorized", requiring authorization for each connection request. Do not accept applications that are unsigned or sent from unknown sources.

